Summary
In this article I am
going to walk you through the steps involved in setting up a network for a
Small/Home office (SOHO). The topics I will cover in this article are - How to configure a Default Gateway (DG)
- How to configure DNS services
- How to configure DHCP services
- Utilize VMWare and Ubuntu
- Default Gateway
- DNS Server
- DHCP Server
- Workstation
Software
Used
- Ubuntu 16.04
- VMWare Workstation 12 Pro
Assumptions
- You are familiar with Linux/UNIX commands.
- If you are using other Linux distributions then some of the commands, packages and/or directory/file names will be different, however, this article will still help you with the concept of configuring a SOHO office.
- You are familiar with virtualization basics (VMWare to be specific)
- You have “sudo” access to log in as “root” to execute the Linux commands mentioned in this article. I am not going to prepend “sudo” for any of the Linux commands mentioned below as that’s implied.
- ipv6 is disabled across the network. I decided to do that to simply the article topic discussion.
Architectural
Diagram
I plan to co-located
the DNS Server and DHCP server on same Ubuntu Virtual Machine (VM) and then
have one Ubuntu VM for Default Gateway and one Ubuntu VM for client
workstation.
NOTE: The DNS and DHCP server
need not be co-located. I am doing it to save time.
General Comments
In the
following sections I will provide detail steps to configure Default Gateway,
DNS and DHCP Server shown in the architectural diagram.
Configure Default Gateway
I plan to configure
an Ubuntu machine to be the default gateway, the steps to do that are mentioned
below
The machine
has two interfaces “ens33” and “ens38”. “ens33” is connected to the internet
and “ens38” is connected to the private home/office network. The “IP” address
assigned to ens38 is a “static” IP and is shown below
The “IP”
address assigned to ens38 is a “dynamic” IP except the DNS Server part which is
pointing to our local DNS Server (IP: 10.0.1.2) and is shown below
NOTE: Interface “ens33” is actually a virtual network card which is getting its private IP: 192.168.164.174 from the VMWare’s DHCP server hence the non-routable private class C address. In the real physical network, “ens33” will be connected to the edge router (possibly via a network switch) with the edge router getting its IP from the ISP, and a firewall device between the default gateway and the edge router.
- Let’s enable NATing with the following command
iptables
-t nat -A POSTROUTING -o ens33 -j MASQUERADE
The above command will enable Masquerading on external interface “ens33”. What that means is for all private network IP subnet – 10.0.1.0/24, it will do NATing to expose the IP packets as one external IP address assigned to interface “ens33”
- Let’s now allow packet forwarding from ingress interface “ens38” to
egress interface “ens33” using the following command
iptables -A FORWARD -i ens38 -o ens33 -j ACCEPT
- Let’s now allow packet forwarding from ingress interface “ens33” to egress interface “ens38” for only packets that are either “Established” or “Related”. Basically what it means is that you cannot have “new” states starting from external interface ens33 to internal private network interface “ens38”.
iptables
-A FORWARD -i ens33 -o ens38 -m state --state RELATED,ESTABLISHED -j ACCEPT
- Let’s install the package “iptables-persistent”, this package depends on “netfilter-persistent” package and will install that package as well
apt-get
install iptables-persistent
The
“netfilter-persistent” is the command that you then use to save and load
iptables rules once changed. “netfilter-persistent” is a service that is
managed by “systemd” daemon and will load files from “/etc/iptables/” for rules
that are saved there. The “/etc/iptables/” folder contains the rules that are
saved by “netfilter-persistent” command options. File “rules.v4” contains rules
for ip4 and file “rules.v6” contains rules for ip6.
- Let’s enable ip forwarding by editing the “/etc/sysctl.conf” file and entering the following line
net.ipv4.ip_forward=1
Enabling
ip forwarding by editing the “/etc/sysctl.conf” file will persist “ip
forwarding” across reboots. If you want to just do it for testing purposes you
can do the same by doing the following
echo
1 > /proc/sys/net/ipv4/ip_forward
Configure DNS Server
I plan to configure
an Ubuntu machine to be the DNS Server, the steps to do that are mentioned
below- Let’s install DNS by executing the following command
apt-get install bind9
- Once the bind9 package is installed then you can configure the following files for DNS services (all the files listed below are found or created under “/etc/bind/” directory)
A few details about the above configuration
a) Section 1 defines the Forward zone for domain “myhome.local” and
b) Section 2 defines the Reverse Zone for 10.0.1.0/24 subnet, which is my private network
ii) db.myhome.local – this file can be named anything but needs to be referenced in the “Section 1” of “named.conf.local” file, Following is the setting for my SOHO network
Forward Zone
Forward Zone
A few details about the above configuration
a) Forward Zone file is needed to allow “name-to-ip” lookups
b) The DNS Server name is “mainsrv01”
c) The DNS Server IP is “10.0.1.2”
a) Forward Zone file is needed to allow “name-to-ip” lookups
b) The DNS Server name is “mainsrv01”
c) The DNS Server IP is “10.0.1.2”
iii) db.10 – this file can be named anything but needs to be referenced in the “Section 2” of “named.conf.local” file, Following is the setting for my SOHO network
Reverse Zone
A few details about the above configuration
a) Reverse Zone file is needed to allow “ip-to-name” lookups
b) We need to have PTR records for every entry of “A” (or ”AAAA” for ipv6) records in the forward zone file
iv) named.conf.options – This is the file where you can define additional configuration for the DNS Server. Following is the setting for my SOHO network
A few details about the above configuration
a) I have defined an Access Control List (acl) called “trusted” that can be used later on in the section “options” to restrict recursive looks up to be allowed for localhost (loopback adapter) and for machines that are connected to local network (our private 10.0.1.0/24 network – done via “localnets”)
b) The acl is extremely important as it’s a security measure against open ended DNS and is used to prevent someone from outside the private 10.0.1.0/24 network from using this DNS server to send recursive queries. Again this is not foolproof but one step towards making your network foolproof.
c) I have also disabled ipv6 to make configuration simpler.
Reverse Zone
A few details about the above configuration
a) Reverse Zone file is needed to allow “ip-to-name” lookups
b) We need to have PTR records for every entry of “A” (or ”AAAA” for ipv6) records in the forward zone file
iv) named.conf.options – This is the file where you can define additional configuration for the DNS Server. Following is the setting for my SOHO network
A few details about the above configuration
a) I have defined an Access Control List (acl) called “trusted” that can be used later on in the section “options” to restrict recursive looks up to be allowed for localhost (loopback adapter) and for machines that are connected to local network (our private 10.0.1.0/24 network – done via “localnets”)
b) The acl is extremely important as it’s a security measure against open ended DNS and is used to prevent someone from outside the private 10.0.1.0/24 network from using this DNS server to send recursive queries. Again this is not foolproof but one step towards making your network foolproof.
c) I have also disabled ipv6 to make configuration simpler.
v) named.conf – Do not make changes in this file to include zones as they are defined in the “named.conf.local” file. For SOHO office network I did not change anything in this file.
The IP address for the DNS server is also static IP and is shown below
Configure DHCP ServerI plan to configure an Ubuntu machine to be the DHCP Server, the steps to do that are mentioned below
The IP address for the DNS server is also static IP and is shown below
Configure DHCP ServerI plan to configure an Ubuntu machine to be the DHCP Server, the steps to do that are mentioned below
- Let’s install DHCP by executing the following command
apt
install isc-dhcp-server
- Let’s configure the interface on which DHCP server will listen for DHCP clients. For that we will edit the “/etc/default/isc-dhcp-server” file and add the following line to it
INTERFACES="ens33"
On my Ubuntu machine
there is only one network card (NIC) named “ens33”.
- Now let’s configure the DHCP settings that DHCP server will send to DHCP clients. For that we will edit the “/etc/dhcp/dhcpd.conf” file and add the following line to it
The above settings define
a) Default lease time
b) Maximum lease time
c) The range of IP pool the DHCP server will use to assign an IP to the client
d) Default gateway
e) Default DNS server
f) Domain name
a) Default lease time
b) Maximum lease time
c) The range of IP pool the DHCP server will use to assign an IP to the client
d) Default gateway
e) Default DNS server
f) Domain name
The IP
address for the DHCP server is same as the DNS Server as I have co-located the
two servers on same Ubuntu VM machine
The DHCP
server will provide the dynamic information for the network cards of all
workstations in the private 10.0.1.0/24 network therefore there is really
nothing you need to do for configuring the workstation network cards. One thing
you have to do for your domain “myhome.local” is that you will have to change
the order of hostname resolution in the “/etc/nsswitch.conf” file as shown
below and you only need to do that because your domain ends with “.local” suffix,
the default name resolution configuration in “/etc/nsswitch.conf” file rejects
any domain that has the “.local” suffix as shown below
#hosts: files mdns4_minimal [NOTFOUND=return]
dns
hosts: files dns
“mdns4_minimal
[NOTFOUND=return]” is the one that rejects name-to-ip lookups for domain that
end with “.local”. That’s the only thing you need to remove from the order as
shown in the second line above (first line is commented out with “#”).
The IP address for
the Workstation is dynamic IP and is shown belowThe DHCP server dynamically assigns the following to the workstation
a) IP (one of the IP from IP range: 10.0.1.100-10.0.1.200)
b) Default Gateway (10.0.1.1)
c) DNS Server (10.0.1.2)
d) Domain Name (myhome.local)
I also started a Windows 7 VM as a workstation just for fun. The dynamic IP address for this workstation is shown below
Miscellaneous things
- The firewall shown in the Architectural Diagram is something that you should consider buying for your SOHO office (get a hardware device for firewall). In this article I just rely on the Linux “iptables” firewall rules on the Ubuntu machine that acts as a default gateway for the private 10.0.1.0/24 network. Also between my private network and public network I have a router. So there is some level of protection as my edge device (which is my default gateway) is not directly connected to my ISP but is connected to my Router which is then connected to my ISP. That is the reason why the external interface “ens33” on my default gateway has a private non-routable class C address 192.168.164.174 (a 192.168.164.0/24 subnet IP address)
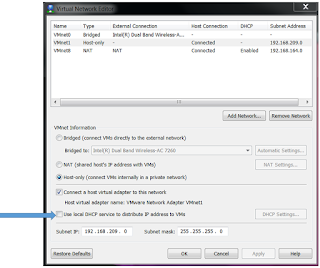
- As I am using VMWare Workstation Pro to configure all the VM, one thing you need to be aware of is that all my private 10.0.1.0/24 network VM’s are in the “host-only” network of my VMWare Workstation Pro. And because I am using my local DHCP server I have disabled DHCP service for the “host-only” network in my VMWare Workstation Pro as shown below

This is
important to disable, you do not want two DHCP servers in your private network.
Conclusion
I hope this
article helped you set up your SOHO office network. Enjoy and have fun.
















No comments:
Post a Comment